------
Update 03/12/2022
Reuters has published new information on this incident, which initially matches the proposed scenario. You can find the update at the bottom of this post.
------
February 24th: at the same time Russia initiated a full-scale attack on Ukraine, tens of thousands of KA-SAT SATCOM terminals suddenly stopped working in several european countries: Germany, Ukraine, Greece, Hungary, Poland...Germany's Enercon moved forward and acknowledged that approximately 5800 of its wind turbines, presumably those remotely operated via a SATCOM link in central Europe, had lost contact with their SCADA server. In the affected countries, a significant part of the customers of Eutelsat's domestic broadband service were also unable to access Internet.
From the very beginning Eutelsat and its parent company Viasat, stated that the issue was being investigated as a cyberattack. Since then, details have been scarcely provided but few days ago I came across a really interesting video in the following tweet.
In the video, the Commander General Michel Friedling confirms that the incident was originated by a cyberattack. However, he also provides a key detail that has the potential to turn a boring DDoS scenario, as some initially pointed out, into something much more interesting: "the terminals have been damaged, made inoperable and probably cannot be repaired"

Based on the information publicly available and my experience researching into SATCOM terminals I'll try to present a plausible explanation for such a destructive attack.
Introduction
Please note that this is merely a speculative exercise, although backed by a realistic technical reasoning...anyway probably I'm totally wrong.
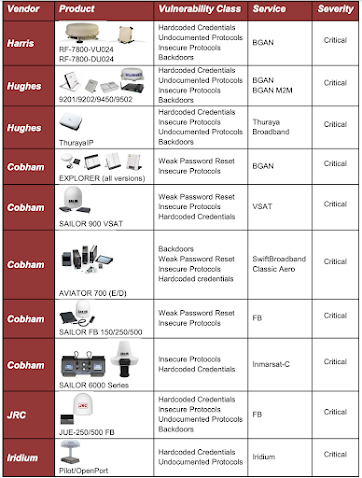
Back in 2014 and then in 2018 I presented at BlackHat USA two different papers mainly focused on evaluating the security posture of multiple SATCOM terminals, by uncovering a plethora of vulnerabilities and real-world scenarios across different sectors. Within these papers the reader can find an introduction to the SATCOM architecture, threat scenarios and some technical terms that will be used during this blog post.
2014 - A Wake-Up call for SATCOM Security
2018 - Last Call for SATCOM Security

In the ground segment of the KA-SAT infrastructure we find 10 gateways distributed across Europe. Please note that the Berlin Gateway is the closest one to Ukraine. Coincidentally, Germany seems to have suffered one the worst parts of the attack.
These Gateway Earth Stations are interconnected using a redundant fiber ring. This backbone also maintains the connectivity with up to 6 telco Points of Presence (POP).
The satellite coverage is divided into the 82 spot beams, each of them is approximately 300km of diameter. As it can be seen in the following image, there are four types of spot beams which enable approximately 240 MHz in both directions (independently for the Forward and Return channels), thus allowing to re-use the slots of available frequencies (1.95 GHz in total, ~((240Mhz*2)*4)) under different polarizations. This throughput requires using multiple Gateway Earth Stations, geographically separated, for properly providing the service.
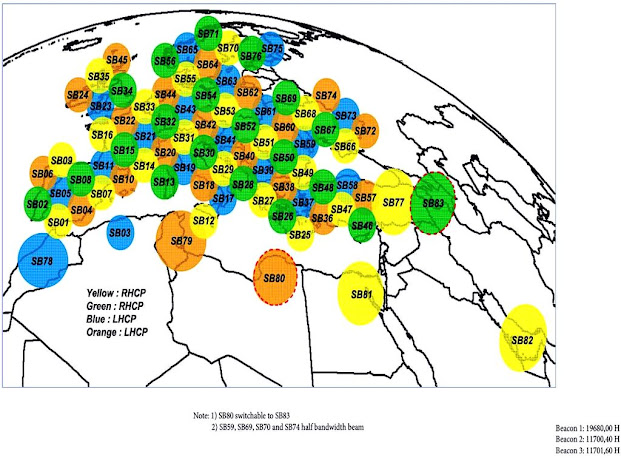
An important detail is that the mappings between the spot beams and the gateways are fixed: each gateway handles a set of 10 different beams.
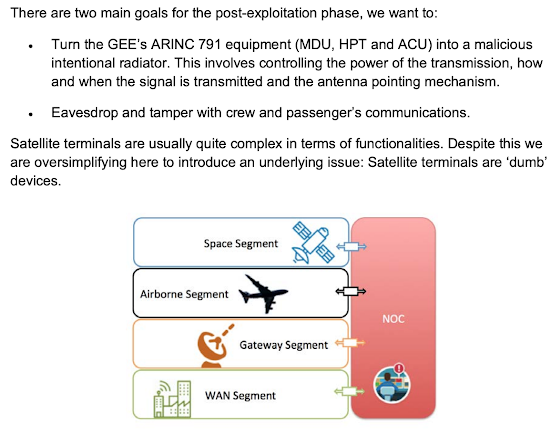
The user terminals are comprised of:
1.- The ODU (Outdoor Unit)
The transmit-receive assembly (TRIA).
2.- The IDU (Indoor Unit)
What do we really know about the attack?
From the information publicly available there are 5 facts that should drive this analysis:
1.- It seems that the attackers originally targeted Eutelsat's KA-SAT SATCOM terminals located in Ukraine but the attack propagated to other countries such as Greece, Germany, Poland, Italy or Hungary.
2.- Apparently, tens of thousands of terminals have been permanently damaged, rendering them inoperable.
3.- It happened at the same time the russian forces initiated the invasion of Ukraine.
4.- It targeted the fixed broadband customers of a civil satellite network, neither maritime nor aviation sectors were affected.
5.- According to the video of the Commander General Michel Friedling, it didn't impact the space segment.
Scenarios
We can initially assess the following scenarios:
1. DDoS
A targeted DDoS attack could have initially explained the temporary disruption of the service, thus complying with all the previous facts. However, it does not provide any explanation for the permanent damage (fact number 2)
2. RF/EM pulse
An attack requiring enough power to deep-fry tens of thousands of terminals at the same time, which are located across multiple countries covering a vast area in the order of thousands of Kms, is not feasible. Moreover, it would have impacted other devices, also immediately triggering a lot of military alarms.
3. 0day in SATCOM terminals publicly exposed.
A remotely exploitable vulnerability in a SATCOM terminal, in addition to an improper network configuration of the satellite provider, is a totally feasible scenario that can be exploited at a certain scale. In 2018 I documented how dozens of commercial aircraft were publicly exposed to the internet through a vulnerable SATCOM infrastructure (see 'Last Call For SATCOM security' - Aviation, Pages 3-19 ).
Please also note that Internet is not the only attack vector that can be used, a malicious terminal connected to a specific SATCOM network may also leverage improper network configurations to attack other terminals. Obviously, this scenario highly depends on the satellite service and operators.
It is interesting that after 4 years, a month ago the NSA released an advisory "
Protecting VSAT Communications" which specifically referenced my 2018 research.
A permanent damage is also technically possible. In 2014, during the '
Wake Up call for SATCOM security' research I reverse engineered a proprietary protocol (Zing) implemented in certain Inmarsat BGAN terminals from Hughes, which allowed multiple privileged operations over the network, including the ability to modify the image of the FPGA controlling the antenna pointing. A successful exploitation rendered the terminal inoperable, pretty much the same scenario we are discussing. In fact, at that time, I successfully tested this destructive attack against the
Hughes 9201 terminal I bought for that research.
Despite all of these indications, I don't think this scenario completely represents what happened in Ukraine and the rest of the affected countries. Certainly, there is a chance that an undocumented feature/0day was exploited but there are other aspects in the attack that do not match: the scale of the attack, the kind of affected systems and its geographical location.
4. A compromised Gateway Earth Station / Network Operations Center.
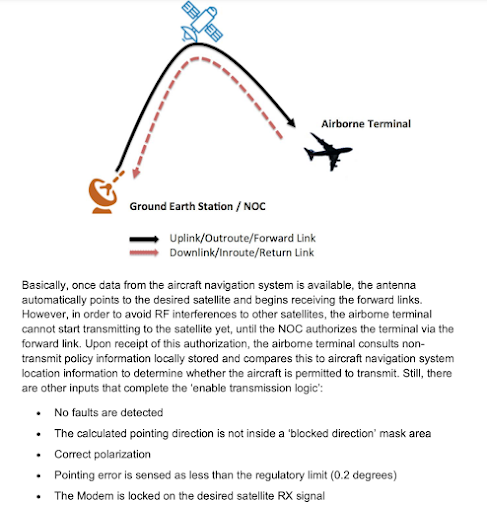
In the 'Last Call For SATCOM Security' research (Pages 20-44) I elaborated a post-exploitation scenario for an airborne SATCOM terminal, intended to turn it into an intentional radiator.
This attack required modifying the firmware to ignore certain specific messages coming from the NOC.
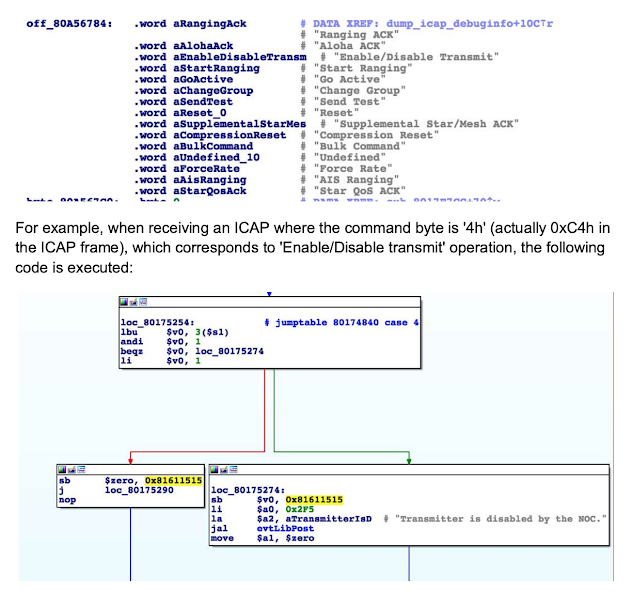
For that research, I reverse engineered Hughes' proprietary ICAP protocol, used to remotely control the SATCOM terminal from the NOC. The image below shows some of the implemented messages, which are self-explanatory in certain cases (i.e 'Enable/Disable transmit')
I was controlling the SATCOM terminal, so my approach was to prevent the NOC from forcing the compromised SATCOM terminal to 'behave' properly (in the context of an intentional radiator payload, terminals are designed in such a way that if you are not locked to the satellite, you shouldn't be transmitting). However, if you've got the NOC under your control, you can achieve the opposite scenario, thus directly attacking the SATCOM terminals within your coverage.
I think that, maybe, what happened in Ukraine is similar to this scenario.
Conclusion
My theory is that attackers somehow managed to compromise/spoof the ground station/NOC in charge of those spot beams covering, at least, Ukraine. At a certain time they abused a legitimate control protocol to issue specific commands to the targeted SATCOM terminals, resulting in the claimed permanent damage. That request may involve disabling the transmitter, corrupting the antenna pointing logic, demod, power params...
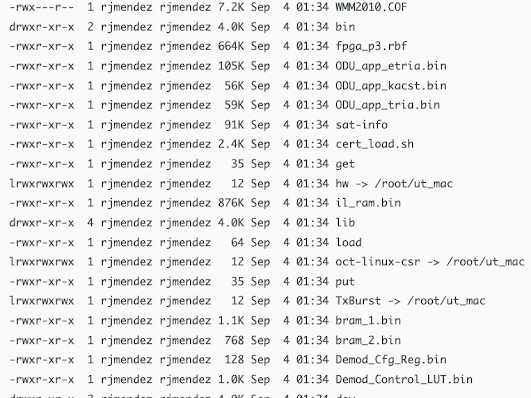
I don't have access to a Surfbeam2 modem, but I found a
writeup of a researcher who dumped its firmware. After reading some of its contents, I'm now even more convinced that there are multiple ways to permanently damage a KA-SAT SATCOM terminal...
Finally, we should bear in mind that, as it has been explained, the KA-SAT infrastructure involves multiple interconnected gateways Earth Stations and a specific number of mappings between beams and gateways. As a result, I would say that probably the Enercon incident, and the disruption that occured in other european countries, were just a 'collateral damage' derived from attacking the main target: Ukraine.
UPDATE - 03/12/2022
According to this statement, the 'management section' of the network was not properly configured so attackers could exploit that attack vector.
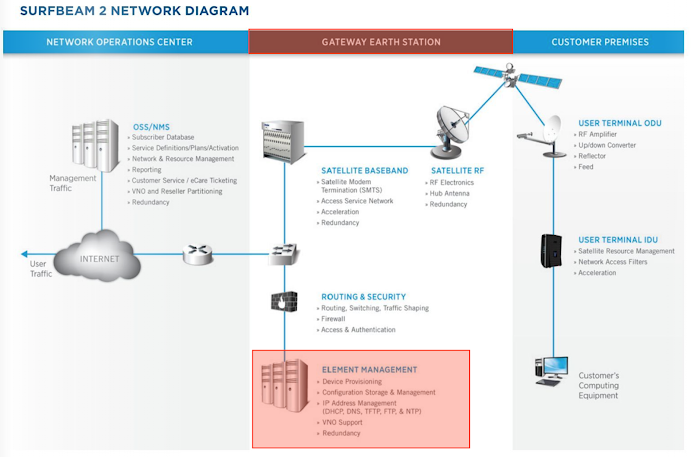
This probably means that the theory herein explained was close to the reality. The attackers likely managed to compromise/spoof a Ground Station (Gateway Earth Station in the picture below), specifically the 'Element Management' section (which likely is sync'ed across gateways), to issue a command by abusing a legitimate control protocol (probably TR-069) that deployed a malicious firmware update to the terminals. For instance, this could have been performed using well-known attacks involving VLANs.
However, it is still a 'mystery' who is behind that particular piece of the Ground Station, as Viasat and Eutelsat are apparently in the 'buck-passing' stage.
So, taking into account it was a network-wide misconfiguration that affected different operators in different countries, we're running out of candidates: maybe Skylogic or maybe the german company
Axiros?